Blogs

SAVIS owns a comprehensive solution suite for digital signing, identity verification, and data encryption that strictly complies with legal regulations
SAVIS GROUP consistently maintains its pioneering position in the field of digital signing and electronic authentication in Vietnam, delivering a comprehensive ecosystem of solutions that strictly adhere to both national and international legal standards. With expertise, high-quality services, and globally recognized technological standards, SAVIS has taken confident steps to solidify its leadership: SAVIS’s digital signing

Build Secure and Private Blockchains with Hyperledger Fabric
What is Hyperledger Fabric? Hyperledger Fabric is an open source, permissioned blockchain framework, started in 2015 by The Linux Foundation. It is a modular, general-purpose framework that offers unique identity management and access control features, which make it suitable for a variety of industry applications such as track-and-trace of supply chains, trade finance, loyalty and

Get Started with Hyperledger Fabric: A Guide to the Main Documentation
Introduction Hyperledger Fabric is a platform for distributed ledger solutions underpinned by a modular architecture delivering high degrees of confidentiality, resiliency, flexibility, and scalability. It is designed to support pluggable implementations of different components and accommodate the complexity and intricacies that exist across the economic ecosystem. We recommend first-time users begin by going through the

Hardware Secure Module (HSM) Adapters Market: Global Opportunity Analysis and Industry Forecast, 2021-2031
The global hardware secure module (HSM) adapters market was valued at $1.3 billion in 2021, and is projected to reach $4.4 billion by 2031, growing at a CAGR of 13% from 2022 to 2031. Hardware security module (HSM) adapters are devices that enable the use of an external HSM with a system or application. An

RSA and ECDSA Certificates: Which Algorithm is Better?
ECDSA and RSA are two of the world’s most widely adopted asymmetric algorithms. However, both these algorithms are significantly different when it comes to the way they function and how their keys are generated. In this blog post, we will briefly examine the differences between RSA and ECDSA certificates to help you understand what they

What is Payment HSM?
A Payment HSM is meant to tighten the layers of security for concealing the sensitive information required by the retail banking industry for payment purposes. Therefore, it is ideal as it functions per the payment industry standards while maintaining adequate security for the cryptographic keys. It is a standard, tamper-resistant, hardened device that can enforce
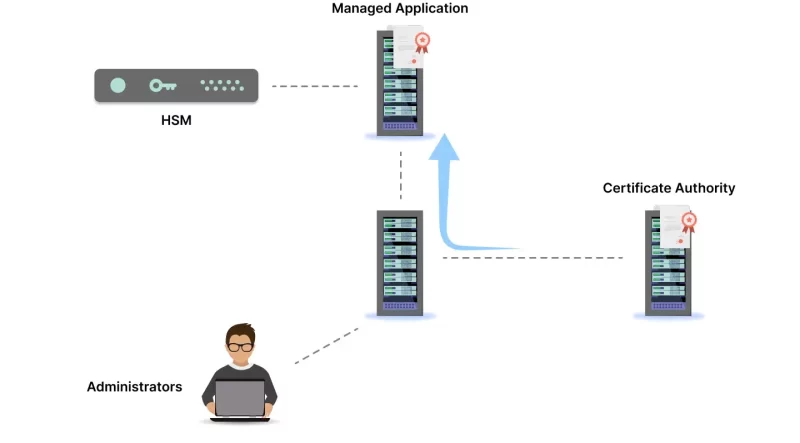
What are HSM devices & their benefits?
A Hardware Security Module refers to a tamper-resistant hardware device meant to strengthen the security of cryptographic keys. It is a special “trusted” device that can perform diverse cryptographic operations in a trusted environment. These devices are ideal for performing decryption, encryption, and authentication for the appropriate use of any application, database, and identity while

ECC Vs RSA Certificate Difference: Decoding the Cryptographic Algorithm
When we talk about securing online communications, ECC and RSA are both encryption algorithms that are inevitable to mention. These algorithms are typically used in SSL/TLS certificates to ensure the security of communication that takes place in the digital space. So naturally, ECC vs. RSA might confuse many. While buying an SSL certificate, the dilemma
What is the Difference between HSM and KMS?
The difference between HSM and KMS is that HSM forms the strong foundation for security, secure generation, and usage of cryptographic keys. At the same time, KMS is responsible for offering streamlined management of cryptographic keys’ lifecycle as per the pre-defined compliance standards. Managing cryptographic relationships in small or big-scale environments seems challenging, given that
